Hey, remember the Apple Vision Pro? For a while there, everyone was talking about Apple’s $3,499 headset being the future of productivity. You’d strap a headset to your face and work on large monitors floating in a “mixed reality” world.
Well, that vision has now officially arrived on Windows PCs, and it’s more than 10 times cheaper. For a mere $299, you can pair a Meta quest headset with a Windows 11 PC and work in a mixed-reality world with floating monitors around you.
So let’s set aside the pricey Apple headsets and skip the wait for Google’s latest attempt at VR. Here’s what it’s like to use the new “Windows Mixed Reality” with an inexpensive Meta headset for productivity. After all: With Microsoft’s HoloLens discontinued, this is the closest thing we’re going to get.
Want to stay up to date on the latest and greatest PC features? Sign up for my free Windows Intelligence newsletter. Plus, get free Windows Field Guide downloads as a special welcome bonus!
What you need for Windows Mixed Reality Link
To try this out, you’ll need a Meta Quest 3 or Quest 3S headset, the company’s latest VR headsets. Again, they’re a lot cheaper than an Apple Vision Pro — and probably a lot cheaper than that upcoming “Project Moohan” headset that will run Google’s new Android XR, too! I tested this out with a Meta Quest 3 headset. (Unfortunately, it doesn’t work with previous-generation Quest 2 headsets.)
You’ll also need a PC running Windows 11. You don’t need the absolute latest hardware, but you do need something at least somewhat recent. I used Microsoft’s latest Surface Laptop. (You can find a complete list of requirements on Microsoft’s website.)
If you have the hardware — and if you already have a recent Meta Quest headset lying around — you’re good to go, and you can set this up very quickly.
How to link your Windows PC and Meta Quest headset
Here at the start of 2025, this feature is still a little experimental. That means you’ll have to go out of your way to activate it. Meta offers detailed instructions, but these quick steps should be all you’ll need to get going:
- On your Windows 11 PC, install the Microsoft’s Mixed Reality Link app from the Microsoft Store.
- On your Meta Quest headset, open the Settings app, select “Advanced,” and activate the “Pair to PC with Mixed Reality Link” setting.
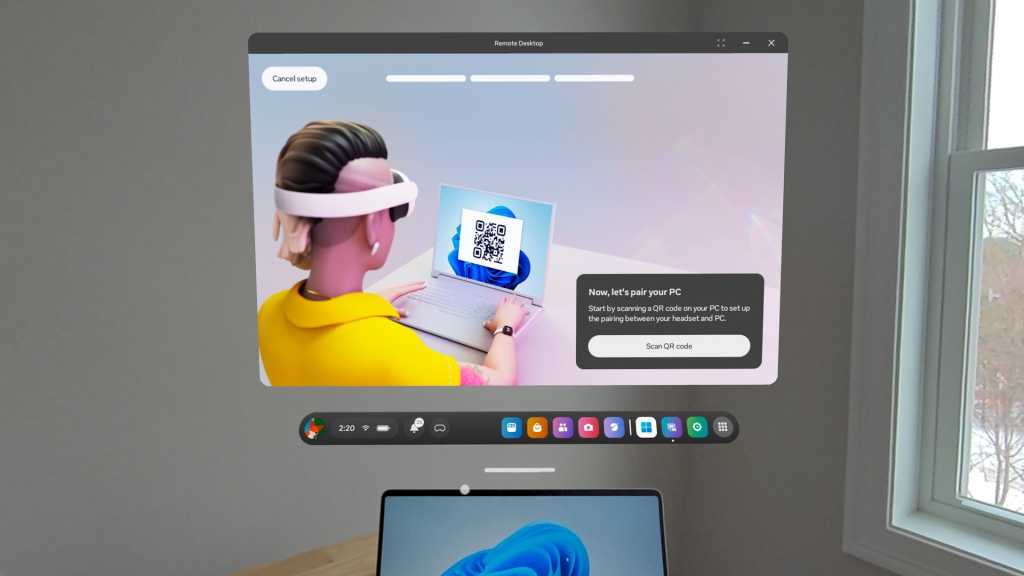
Then, while wearing the headset and using passthrough (Mixed Reality) mode, you can just look at a Windows 11 PC, and you’ll see a floating “Pair” button you can click to pair your headset with your PC.
The first time you pair, you’ll be asked to press Windows+Y. Your PC will show a QR code, and your headset will scan it — and then, the two devices will be linked. From that point forward, you can just look at the PC while wearing the headset and select “Pair.”
Chris Hoffman, IDG
A Windows desktop, floating in front of your face
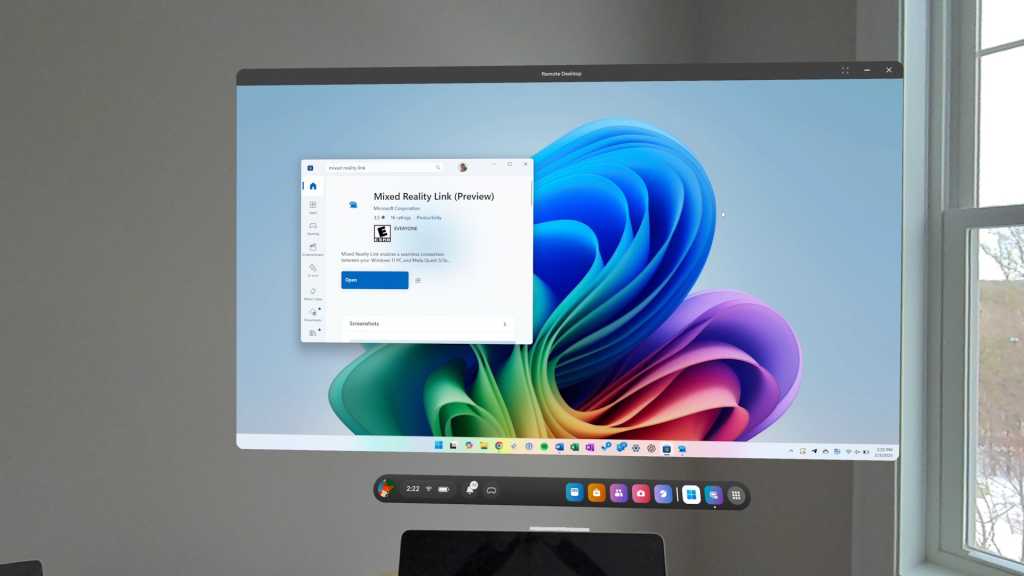
While paired, you’ll see your PC’s desktop pop up as a floating window in passthrough mode (just like other apps in the Meta Quest’s Horizon OS). You can type on your computer’s keyboard normally — and use its mouse — to control Windows and your applications.
It works better than you might expect! There isn’t much latency — despite the wireless connection, it’s a very responsive interface that feels great to use.
You can use “theater mode” to expand the desktop to take up more of your vision, if you like. That lets you place the desktop somewhere you want it in space, walk away, then walk back to it.
Productivity aside, this has the potential for all sorts of engaging entertainment use for mid-work-day breaktimes or moments of travel. If you enjoy the thought of watching a movie on a big virtual screen while wearing a headset, you can definitely do that with this setup. I pulled up YouTube, switched to full-screen mode, and toggled theater mode for the whole experience. It was more than a little impressive to see the entire video filling my field of vision. Similarly, you could play PC games while wearing the headset — or, of course, watch official work-related demo videos and presentations. It’s a very different experience from using a small laptop display.
The only real downside is having to wear a headset the entire time you’re watching.
Chris Hoffman, IDG
How does Mixed Reality Link work for productivity?
So the $1 million question: Does Microsoft’s Mixed Reality Link and a Meta Quest headset really make you more productive?
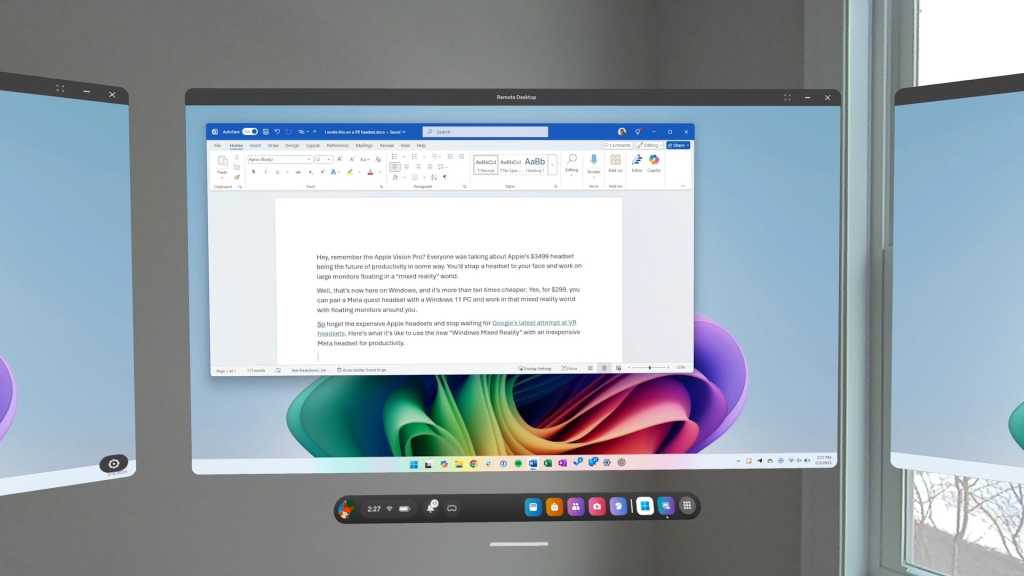
The biggest benefit is the ability to add extra virtual displays beyond what you’d have in the physical world. I used my Surface Laptop, which didn’t have any external monitors connected. With a few presses of buttons on the Meta Quest’s controllers, I was able to add two extra displays that floated off to the sides of my main display, giving myself some extra virtual space for working. I’m able to enjoy a spacious three-display setup in the Mixed Reality interface, although I just have the one small physical screen.
I’ll be honest, though: I’ve never fully understood why I would want to do my productivity-oriented work with a headset strapped to my head. That was my big concern about Apple’s Vision Pro, and it’s my big challenge here. I do think Meta’s Quest headset is neat for VR games and workout apps. But we’re not talking about using VR with a sense of presence here — we’re talking about using a two-dimensional Windows desktop interface floating in space.
Chris Hoffman, IDG
That’s one of the most significant downsides to this setup — that we’re talking about a two-dimensional desktop. You won’t be using an immersive VR application like Google Earth VR over Windows Mixed Reality link. You’ll just get access to the same standard two-dimensional applications you use on your Windows desktop. (There are other solutions for using PC VR apps with a Quest headset, but Mixed Reality Link doesn’t simplify the process.)
Compared to other mixed-reality headset platforms, the fact that you’re just dealing with your PC’s desktop is also an advantage. There’s no need to set up your productivity workflow on a new device — you’re just getting access to the desktop interface you already use. So, if you do want this sort of interface for productivity or PC desktop use in general, good news: It’s here, and you can get it today for a few hundred bucks!
Personally, I’ve been writing this entire article with Microsoft Word floating in front of my face while wearing the headset. And, while it worked really well, I’m looking forward to removing the headset and giving my face a break.
Of course, this is just “version one” of this experience. In the future, we might eventually see incredibly lightweight and comfortable “smart glasses” that are easier to wear for extended periods of time. Perhaps that’s the future of computing — a floating Windows desktop on our smart glasses.
Or…, perhaps not. But, with Apple and Google making big bets on mixed-reality headset experience, it’s nice to know that there’s a version of that spatial computing experience already available for us Windows PC users, too.
Let’s stay in touch! Sign up for my free Windows Intelligence newsletter today. You’ll get three new things to try every Friday and free in-depth Windows Field Guides as a special welcome gift.