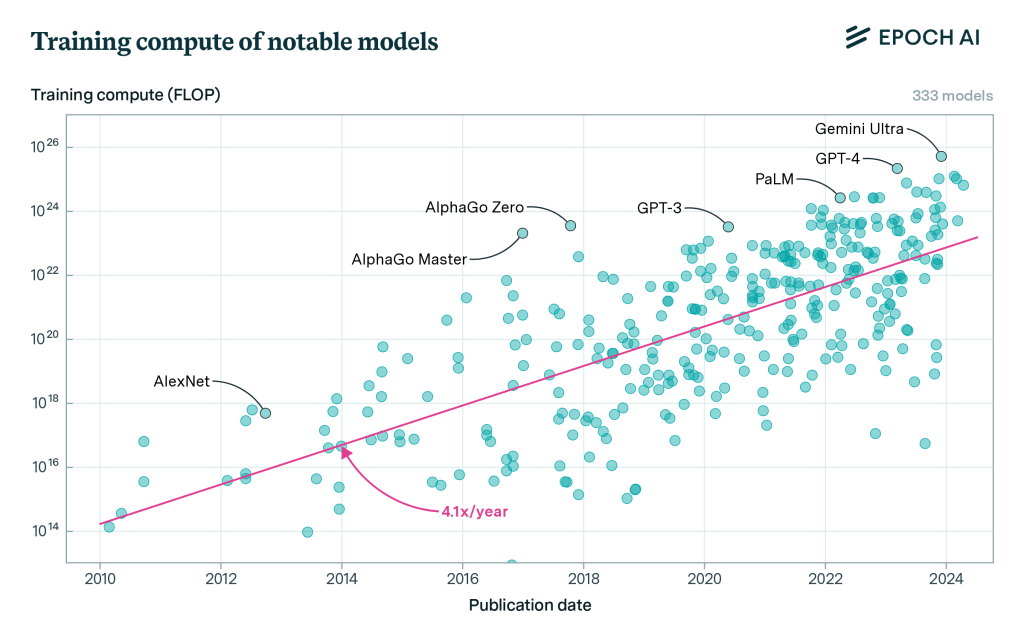
Excel’s Ribbon is great for finding everything you might ever want to do in a spreadsheet, particularly things you don’t do frequently, like managing and querying data connections or automatically grabbing geographic statistics from the internet and inserting them into cells.
But if you’re looking to do things fast, you’ll find keyboard shortcuts far more useful. Why bother to lift your hands from the keyboard if you want to open or close a file, apply formatting to cells, navigate through workbooks, undo and redo actions, calculate all worksheets in all open workbooks, and more? With keyboard shortcuts you won’t have to.
There are keyboard shortcuts to accomplish a vast array of tasks in the Excel desktop client, in both the Windows and Mac versions. (Fewer shortcuts are available for the Mac, but you can create your own custom keyboard shortcuts if you like.)
We’ve listed the shortcuts we’ve found the most useful below. Most work whether you’re using a subscription (Microsoft 365/Office 365) or non-subscription version of Excel. For even more shortcuts, see Microsoft’s Office site.
Useful Excel keyboard shortcuts
Note: On Macs, the ⌘ key is the same as the Command or Cmd key. Also note that with many Mac keyboards, you must press the Fn key in addition to a function key.
General shortcuts
| Action | Windows key combination | Mac key combination |
| Create a new workbook | Ctrl-N | ⌘-N |
| Open a workbook | Ctrl-O | ⌘-O |
| Save a workbook | Ctrl-S | ⌘-S |
| Close a workbook | Ctrl-W | ⌘-W |
| Print a workbook | Ctrl-P | ⌘-P |
| Insert a new worksheet (tab) | Alt-Shift-F1 | Shift-Fn-F11 |
| Display the Find dialog box | Ctrl-F | Control-F |
| Display the Go To dialog box | F5 | Fn-F5 |
| Undo the last action | Ctrl-Z | ⌘-Z or Control-Z |
| Redo the last action | Ctrl-Y | ⌘-Y or Control-Y |
| Insert or edit a cell comment | Shift-F2 | ⌘-Shift-Fn-F2 |
| Select all cells that contain comments | Ctrl-Shift-O | |
| Spell-check the active worksheet or selected range | F7 | Fn-F7 |
Worksheet navigation
| Action | Windows key combination | Mac key combination |
| Move one screen up / down | PgUp / PgDn | Page Up / Page Down or Fn-up arrow / Fn-down arrow |
| Move one screen to the left / right | Alt-PgUp / Alt-PgDn | Option-Page Up / Option-Page Down or Fn-Option-up arrow / Fn-Option-down arrow |
| Move one worksheet tab to the left / right | Ctrl-PgUp / Ctrl-PgDn | Control-Page Down / Control-Page Up or Option-right arrow / Option-Left arrow |
| Move one cell up / down | up arrow / down arrow | up arrow / down arrow |
| Move to the next cell to the right | Tab | right arrow |
| Move to the cell to the left | Shift-Tab | left arrow |
| Move to the beginning of a row | Home | Home or Fn-left arrow |
| Move to the beginning of a worksheet | Ctrl-Home | Control-Home or Control-Fn-Left arrow |
| Move to the last cell that has content in it | Ctrl-End | Control-End or Control-Fn-right arrow |
| Move to the word to the left while in a cell | Ctrl-left arrow | ⌘-left arrow |
| Move to the word to the right while in a cell | Ctrl-right arrow | ⌘-right arrow |
| Display the Go To dialog box | Ctrl-G or F5 | Ctrl-G or Fn-F5 |
| Switch between the worksheet, the Ribbon, the task pane, and Zoom controls | F6 | Fn-F6 |
| If more than one worksheet is open, switch to the next one | Ctrl-F6 | ⌘-~ |
Working with data
| Action | Windows key combination | Mac key combination |
| Select a row | Shift-Spacebar | Shift-Spacebar |
| Select a column | Ctrl-Spacebar | Control-Spacebar |
| Select an entire worksheet | Ctrl-A or Ctrl-Shift-Spacebar | ⌘-A |
| Extend selection by a single cell | Shift-arrow key | Shift-arrow key |
| Extend selection down / up one screen | Shift-PgDn / Shift-PgUp | Shift-PgDn / Shift-PgUp or Shift-Fn-down arrow / Shift-Fn-up arrow |
| Extend selection to the beginning of a row | Shift-Home | Shift-Home or Shift-Fn-left arrow |
| Extend selection to the beginning of the worksheet | Ctrl-Shift-Home | Control-Shift-Home or Control-Shift-Fn-left arrow |
| Hide selected rows | Ctrl-9 | ⌘-9 or Control-9 |
| Unhide hidden rows in a selection | Ctrl-Shift-( | ⌘-Shift-( or Control-Shift-( |
| Hide selected columns | Ctrl-0 | ⌘-0 or Control-0 |
| Unhide hidden columns in a selection | Ctrl-Shift-) | ⌘-Shift-) or Control-Shift-) |
| Copy cell’s contents to the clipboard | Ctrl-C | ⌘-C or Control-C |
| Copy and delete cell’s contents | Ctrl-X | ⌘-X or Control-X |
| Paste from the clipboard into a cell | Ctrl-V | ⌘-V or Control-V |
| Display the Paste Special dialog box | Ctrl-Alt-V | ⌘-Option-V or Control-Option-V |
| Finish entering data in a cell and move to the next cell down / up | Enter / Shift-Enter | Enter / Shift-Enter |
| Cancel your entry in a cell | Esc | Esc |
| Use Flash Fill to fill the current column based on adjacent columns | Ctrl-E | Control-E |
| Insert the current date | Ctrl-; | Control-; |
| Insert the current time | Ctrl-Shift-; | ⌘-; |
| Display the Create Table dialog box | Ctrl-T or Ctrl-L | Control-T |
| When in the formula bar, move the cursor to the end of the text | Ctrl-End | ⌘-End or ⌘-Fn-right arrow |
| When in the formula bar, select all text from the cursor to the end | Ctrl-Shift-End | ⌘-Shift-End or ⌘-Shift-Fn-right arrow |
| Display Quick Analysis options for selected cells that contain data | Ctrl-Q | |
| Create, run, edit, or delete a macro | Alt-F8 | Option-Fn-F8 |
Formatting cells and data
| Action | Windows key combination | Mac key combination |
| Display the Format Cells dialog box | Ctrl-1 | ⌘-1 or Control-1 |
| Display the Style dialog box (Windows) / Modify Cell Style dialog box (Mac) | Alt-‘ | Option-‘ |
| Apply a border to a cell or selection | Ctrl-Shift-& | ⌘-Option-0 |
| Remove a border from a cell or selection | Ctrl-Shift-_ (underscore) | ⌘-Option– (hyphen) |
| Apply the Currency format with two decimal places | Ctrl-Shift-$ | Control-Shift-$ |
| Apply the Number format | Ctrl-Shift-~ | Control-Shift-~ |
| Apply the Percentage format with no decimal places | Ctrl-Shift-% | Control-Shift-% |
| Apply the Date format using day, month, and year | Ctrl-Shift-# | Control-Shift-# |
| Apply the Time format using the 12-hour clock | Ctrl-Shift-@ | Control-Shift-@ |
| Insert a hyperlink | Ctrl-K | ⌘-K or Control-K |
Working with formulas and functions
| Action | Windows key combination | Mac key combination |
| Begin a formula | = | = |
| Insert a function | Shift-F3 | Shift-Fn-F3 |
| Insert an AutoSum function | Alt-= | ⌘-Shift-T |
| Accept / insert function with AutoComplete | Tab | Tab-down arrow |
| Cancel an entry in the cell or formula bar | Esc | Esc |
| Edit active cell, put insertion point at end | F2 | Control-U |
| Toggle between displaying formulas and cell values | Ctrl-` | Control-` |
| Cycle formula references among absolute, relative, and mixed | F4 | ⌘-T or Fn-F4 |
| Copy and paste the formula from the cell above into the current one | Ctrl-‘ | Control-Shift-“ |
| Calculate the current worksheet | Shift-F9 | Shift-Fn-F9 |
| Calculate all worksheets in all workbooks that are open | F9 | Fn-F9 |
| Expand or collapse the formula bar | Ctrl-Shift-U | Control-Shift-U |
Ribbon navigation
Excel for Mac does not have keyboard shortcuts for the Ribbon.
| Action | Windows key combination |
| Display Ribbon shortcuts | Alt |
| Go to the File tab | Alt-F |
| Go to the Home tab | Alt-H |
| Go to the Insert tab | Alt-N |
| Go to the Page Layout tab | Alt-P |
| Go to the Formulas tab | Alt-M |
| Go to the Data tab | Alt-A |
| Go to the Review tab | Alt-R |
| Go to the View tab | Alt-W |
| Put cursor in the Tell Me or Search box | Alt-Q |
| Go to the Chart Design tab when cursor is on a chart | Alt-JC |
| Go to the Format tab when cursor is on a chart | Alt-JA |
| Go to the Table Design tab when cursor is on a table | Alt-JT |
| Go to the Picture Format tab when cursor is on an image | Alt-JP |
| Go to the Draw tab (if available) | Alt-JI |
| Go to the Power Pivot tab (if available) | Alt-B |
Looking for more help with Excel for Windows? If you have an Office subscription, see “Excel for Office 365/Microsoft 365 cheat sheet.” If you have a non-subscription version of Office, see “Excel 2016 and 2019 cheat sheet.” We’ve also got cheat sheets for an array of other Microsoft products, including older versions of Office.
Related: