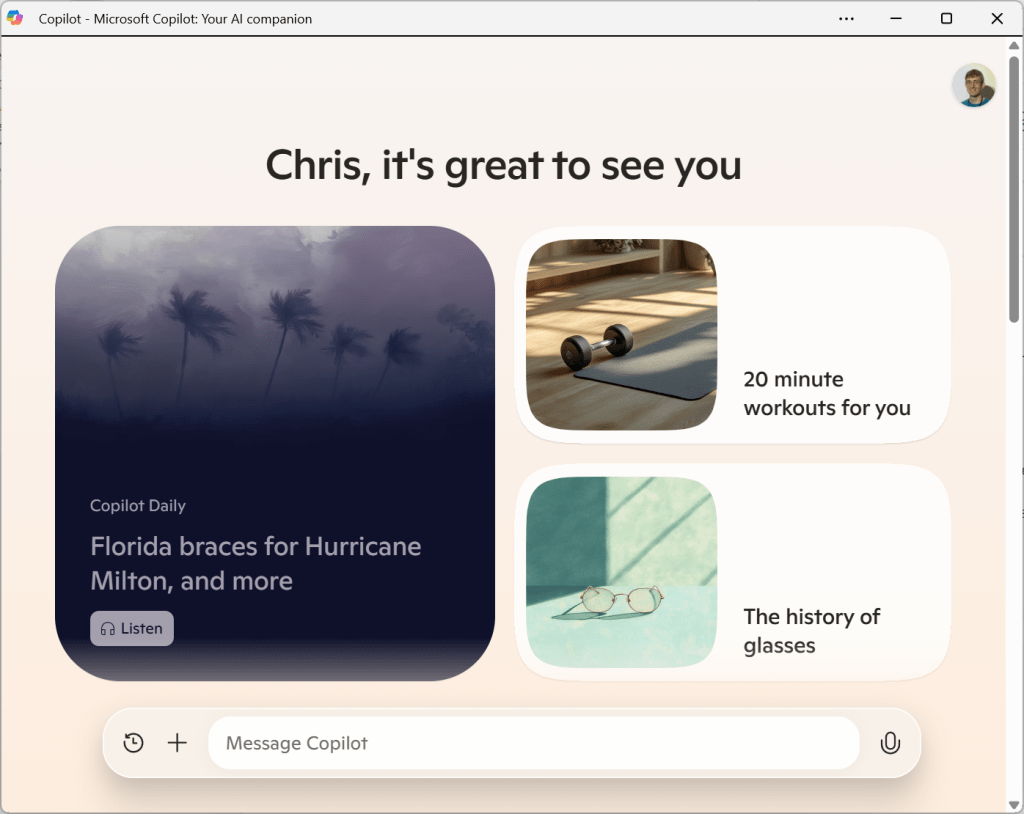
“It’s great to see you!”
Microsoft’s Copilot AI chatbot underwent a transformation last week, morphing into a simplified pastel-toned experience that encourages you…to just chat.
“Hey Chris, how’s the human world today?”
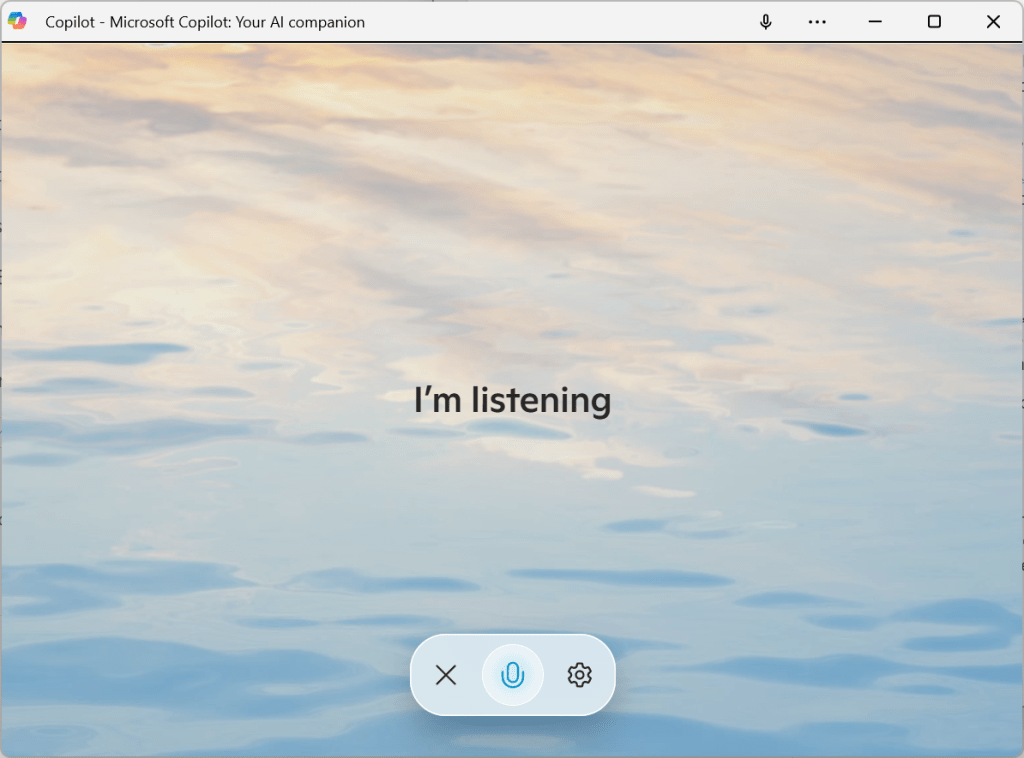
That’s what I heard after I fired up the Copilot app on Windows 11 and clicked the microphone button, complete with a calming wavey background. Yes, this is the type of banter you get with the new Copilot.
We’ve gone from AI search assistant straight to the movie Her. The comparison has been made before, but it’s clearly what OpenAI’s Sam Altman and others in the industry are striving for.
Want more information about the future of Windows? My free Windows Intelligence newsletter delivers all the best PC advice straight to your email inbox. Plus, you’ll get free in-depth Windows Field Guides as a special welcome bonus!
From Bing Chat to ‘I can’t search the web’
Copilot’s October transformation is a dizzying turn for a chatbot that started out as “Bing Chat” — an AI-assisted way to search the web. In fact, Microsoft at one point cracked down on people using Bing Chat to just, well, chat — limiting the number of messages and dispatching with the “Sydney” personality that generated the crazy headlines.
Then, just over a year ago, I sat a few feet away while Microsoft CEO Satya Nadella unveiled the Copilot branding on stage. While it was billed as “your everyday AI companion,” it was more about accomplishing tasks and finding information than having an extended conversation about how your day went.
Now, the Copilot app across Windows PCs, the web, Android, and iPhone is something totally new. It encourages you to just tap the microphone and talk. The text box now encourages you to “Message Copilot,” as if you were about to chat with the SmarterChild chatbot on AOL Instant Messenger 20 years ago.
Oh — and it can’t even search the web for information anymore, at least not by using voice commands. Yes, the latest version of Copilot is truly a mixed bag.
Chris Hoffman, IDG
Meet the new Copilot: A conversation partner
If you haven’t tried the latest Copilot experience, you’ll be surprised to see how different it is. The new iteration has been gradually rolling out across the Copilot app for Windows, the Copilot website, and the Copilot mobile apps.
When you fire it up, you’ll be asked your name and to choose from one of four voices. Then, you talk — just click or tap the microphone icon.
Microsoft is a big investor in OpenAI, and Bing Chat and Copilot have always essentially been a rebranded ChatGPT experience. The new Copilot is a spitting image of the GPT-4o conversational experience OpenAI showed off earlier in 2024. You just start talking, the AI will respond and you can even interrupt it whenever you like, having somewhat of a fluid conversation.
On one level, it’s impressive technology. On another level — this is still an AI chatbot. While I understand the argument for using AI in many situations, I’m not sure I feel like just sitting around and having a long conversation with a chatbot. Additionally, over the past few days of using Copilot, I’ve had a lot of moments where the conversation seems to freeze. I’ll be talking with Copilot and it will go silent, possibly while also displaying an error message.
It’s not as stable as it should be, but hopefully it’ll get better.
Forget productivity — let’s chat!
The most surprising missing feature is web search. Yes, if you ask Copilot to find information online, it will talk about all the great ways you can go find it yourself. If you ask why it can’t do the search for you, Copilot will inform you that web search functionality has been removed in an update. However, it appears it can still search the web if you type text messages to it rather than speaking.
The good news is that you still appear to be able to access the old “Bing Chat-style” Copilot experience: Just head to Bing.com/chat.
AI image generation has also taken a hit. We at The Intelligence occasionally use Copilot to generate some decorative images for our own website. Copilot’s AI image generation experience — which uses OpenAI’s Dall-E 3 AI image generator under the hood — is less compelling now. It will only generate one image at a time, for example, instead of four to choose from. (You get a lot more options by using the Microsoft Designer website for AI image generation.)
Plus, some things just don’t work well using the voice interface. I asked Copilot, for instance, if it could generate some code. “I’m not going to rattle off code snippets or anything. I wouldn’t want to mess with your flow,” it said confidently. Copilot can’t seem to stop the voice conversation to show you something. But you can still get Copilot to generate that sort of thing by typing a text prompt.
Microsoft does offer some early attempts at Copilot providing useful information before you ask here. There’s a “Copilot Daily,” a little AI-generated spoken update that describes a few of the latest news stories to you. If you’d like to start your day having AI choose and summarize a few news stories for you, it can certainly do that!
Chris Hoffman, IDG
Another fresh start for Copilot
Microsoft seems to be in a constant state of trying to figure out what it wants Copilot to be. The concept started as an AI tool built into Bing, complete with Bing branding. Then, it became a productivity tool named Copilot — still for getting things done! Now, Microsoft thinks people might just want to chat.
Microsoft already showed off voice and vision for the Copilot experience. Copilot sits right there on your desktop as you browse, seeing what you see and answering questions about it. It’s like the Minecraft demo Microsoft showed off, which had Copilot watching the gameplay and providing input.
Vision isn’t here yet — there’s only voice support. And it does seem likely that Microsoft will continue adding features like web search.
Another big change involves a shift toward a “single conversation” model. You aren’t continually creating new conversations and starting over. Instead, you’re focusing on a single ongoing conversation — which is convenient, in a way, as Copilot can remember what you were talking about a few days ago.
Still, there’s something odd going on here. ChatGPT and Bing Chat initially felt like productivity tools. You really had to prompt them properly to get useful output, but if you did things right, it would (sometimes, and with varying levels of accuracy) deliver them. Bing Chat was positioned for searching the web!
Now, Microsoft is going in the other direction. Many of these changes have made Copilot less useful as a productivity tool. But it’s a lot better if you want to just sit down and have an extended conversation with your computer. In some ways, it’s like a more useful Siri or Google Assistant interface — though at least smartphone voice assistants can search the web for you with your voice!
A year ago, I wrote that you were probably going to use Copilot wrong because AI chatbots are more story-based than fact-based. They’re more story-generation engines than they are fact-finding tools. That’s what was odd about the first chatbots being positioned as productivity tools. Now, Copilot is becoming more of a conversation partner — a role it probably fills better.
But do you want an AI-based conversation partner in your life? Microsoft — along with seemingly every other company — is betting the answer is yes. It’s a bold strategy; we’ll see if it pays off.
Don’t take my word for it, though — fire up Copilot and talk with it yourself. The new experience is live in English in the United States, Canada, the United Kingdom, Australia, and New Zealand and will be arriving in more languages and countries soon.
Get even more Windows tips, tricks, and app recommendations with my Windows Intelligence newsletter — three things to try every Friday. Plus, get free copies of Paul Thurrott’s Windows 11 and Windows 10 Field Guides (a $10 value) for signing up.